Protect Intellectual Property (IP)
Corporations are repositories of high-value data. This includes internal communications, product research, proprietary source code, employee data (PII), financial records, and contract planning.
Get a competitive edge with HSM-backed encryption that secures critical assets and ensures enterprise-wide compliance.

Corporate databases are high-value targets for cybercriminals, hacktivists, and competitors. To keep them safe, Futurex provides hardware security modules (HSMs) deployed on-premises or in the cloud. Our FIPS 140-2 Level 3-validated HSMs encrypt data, manage key and certificate lifecycles, and centralize cryptographic management. The result is confidential intra-office communication, secure storage and authentication of intellectual property, and compliance with national and international requirements for data retention. Our solutions include database encryption, user access control, authentication of intellectual property, national and international compliance, and secure communication.
The health of a corporate security infrastructure depends on strong encryption. Corporations must guard against attack vectors both inside and outside the organization. Your cryptographic infrastructure must be powerful yet scalable enough to adapt to changing business needs. You need a broad yet reliable range of cryptographic functions to encrypt large amounts of data in transit and at rest.
Futurex delivers HSMs on-premises or in the cloud to secure corporate data at every point. Our HSMs encrypt data in transit and at rest, making it indecipherable to attackers. Our enterprise key management servers establish the public key infrastructure (PKI) to authenticate Intellectual Property (IP) and secure intra-office communications, doing this all through intuitive user interfaces and with industry-leading technology.
The Futurex FIPS 140-2 3-validated hardware security modules (HSMs) encrypt data transmission and storage. You can scale their processing power to an industry-leading 25,000 transactions per second (TPS). Their range of encryption functions is broad, including point-to-point encryption (P2PE) and vaultless tokenization of data.
Futurex FIPS 140-2 Level 3-validated key management servers generate asymmetric public and private key pairs. This is the basis for public key infrastructure (PKI) and certificate authority (CA). Establishing a PKI and CA allows you to digitally sign devices and code, authenticate intellectual property (IP), control user access, and more.
Corporations are repositories of high-value data. This includes internal communications, product research, proprietary source code, employee data (PII), financial records, and contract planning.
Threats to a corporation’s security include cybercriminals seeking to commit fraud, hacktivists wishing to leak data, rivals seeking competitive intelligence, and even employees disregarding best practices.
Futurex offers the most versatile and scalable cryptographic platform, with full redundancy, automatic fail-over, hard drive replication, disaster recovery, one-click cloud migration, and more.
A Public Key Infrastructure enables users or devices to securely transmit sensitive data over insecure public spaces such as the internet by using asymmetric key pairs consisting of a public and private key. The data is transmitted with a public key and then decrypted with the private key in a secure environment. With a PKI, this data is both encrypted and authenticated, so the receiving entity can be assured of the data integrity.
Public key infrastructures use public and private key pairs generated and distributed by a trusted device known as a certificate authority (CA). Certificate authorities, often validated by third-party auditors, generate digital certificates and assign them to the electronic devices that make up the PKI.
A Public Key Infrastructure allows users or devices to securely transmit sensitive data over insecure public spaces such as the internet, using asymmetric key pairs, which consist of a public and private key. The data is transmitted with a public key, and then decrypted with the private key in a secure environment. With a PKI, this data is both encrypted and authenticated, enabling the receiving entity to be assured of the integrity of the data.
Public key infrastructures use public and private key pairs that are generated and distributed by a trusted device known as a certificate authority (CA). Certificate authorities, which are often validated by third-party auditors, are used to generate digital certificates, and assign them to the electronic devices that make up the PKI.
A Public Key Infrastructure allows users or devices to securely transmit sensitive data over insecure public spaces such as the internet, using asymmetric key pairs, which consist of a public and private key. The data is transmitted with a public key, and then decrypted with the private key in a secure environment. With a PKI, this data is both encrypted and authenticated, enabling the receiving entity to be assured of the integrity of the data.
Public key infrastructures use public and private key pairs that are generated and distributed by a trusted device known as a certificate authority (CA). Certificate authorities, which are often validated by third-party auditors, are used to generate digital certificates, and assign them to the electronic devices that make up the PKI.
Using Futurex enterprise key management servers, corporate administrators can establish a PKI to secure private keys and create an offline root certificate authority (CA). The offline root certificate establishes a working certificate that can digitally sign intellectual property such as research, knowledge base items, and code. It can also authenticate users to prevent unauthorized access to the network. Like the PKI, having a CA in your corporate security infrastructure is essential to protecting corporate assets and mitigating cybersecurity risks.
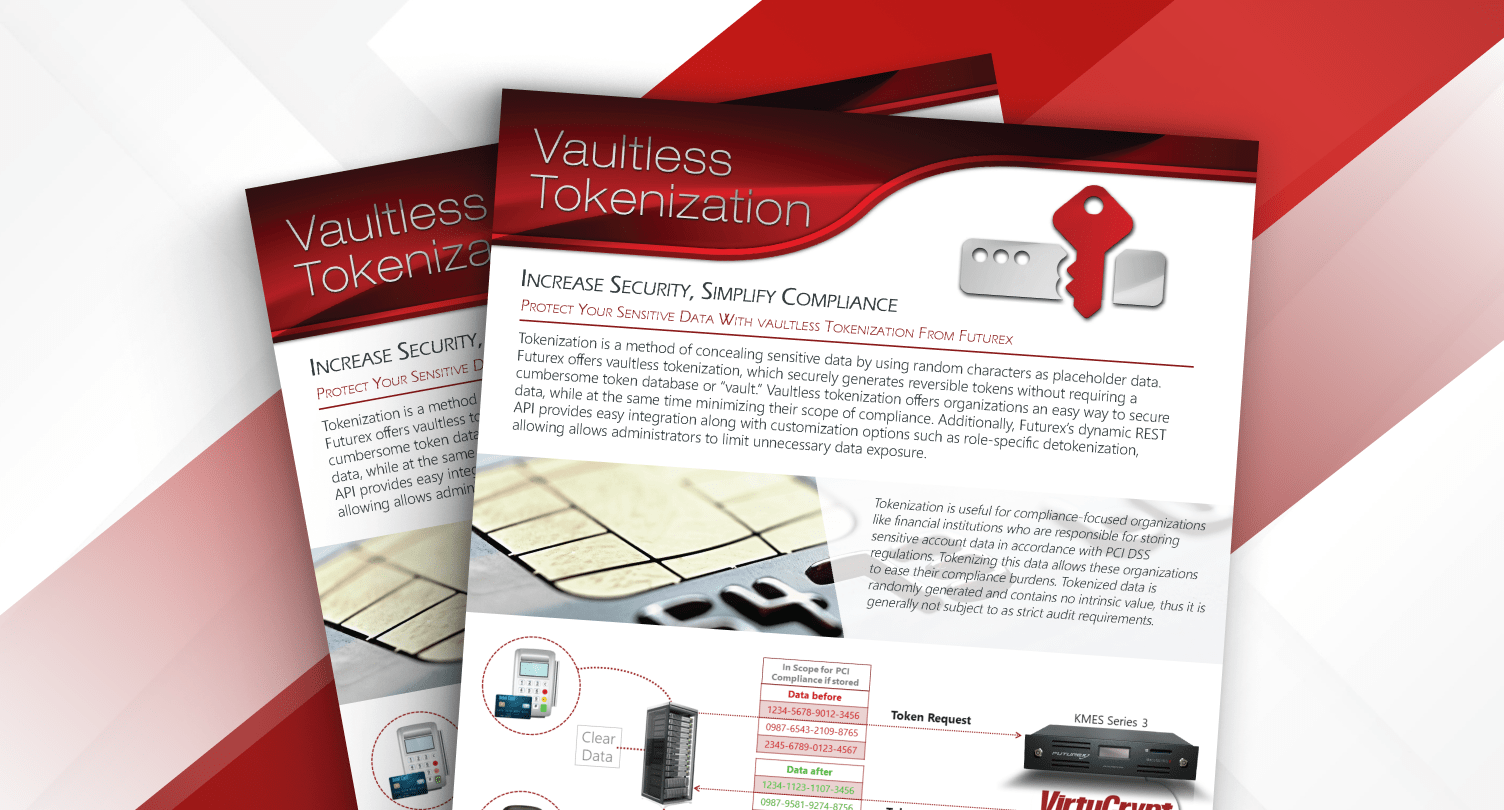
Tokenization replaces sensitive data with a string of identifying characters, known as tokens, for storage. The two most common approaches to tokenizing data are hash-based message authentication code (HMAC) and encryption-based. Most users prefer the encryption method in cases where they need to reverse the tokenization for any reason. Tokenization effectively removes the burden of multiple parties storing sensitive data in the clear while still allowing easy access to authorized applications and users.
Vaultless tokenization is the Futurex advanced method of tokenization. A token vault is a database containing the clear data represented by tokens, and the existence of such a vault represents a significant potential risk. Vaultless tokenization removes the token vault from the equation. The Futurex key management platform tokenizes data before storage and detokenizes it on retrieval. This way, data is never stored in the clear and is indecipherable if a data breach occurs.
We know compliance is a vital factor when choosing a provider, which is why we designed Futurex solutions from the ground up to adhere to all major industry compliance standards, including PCI DSS, FIPS 140-2 Level 3, and PCI HSM.
The Federal Information Processing Standards (FIPS) is a U.S. government security standard used to accredit cryptographic modules that protect sensitive but unclassified information. The Level 3 aspect adds requirements for physical tamper resistance, tamper responsiveness, and identity-based authentication.
Multiple instances of HSMs deployed in the cloud or on-premises eliminate single points of failure and enable you to perform updates and maintenance with no downtime. At the same time, it affords a risk-free backup and recovery method.
Device management has never been simpler. Use one-click migration to seamlessly move cybersecurity infrastructure from on-premises to cloud HSMs. Instantly provision, configure, and manage HSMs in the VirtuCrypt Intelligence Portal (VIP).
Futurex products, validated as Secure Cryptographic Devices (SCD), promote robust cyber security through tamper-responsiveness, reinforced chassis, dual bezel locks, and logical restrictions such as role-based permissions and dual control.
Encrypt files or data fields at the application level to reduce the risk of exposing sensitive information in the clear.

Balance security and availability to protect data across all devices and networks with TDE and hardened data encryption.
Encrypt files at rest before public transfer and control the key so that even your cloud provider can't access them.

Protect valuable data with randomly generated, vaultless tokens to reduce risk and complexity.

Use powerful and scalable HSMs and key management servers to encrypt and protect data in transit and at rest.

Achieve email security and establish PKI and certificate authority by using HSMs to authenticate end users.
Integrate with 3rd party applications to protect application secrets, passwords, and keys, securely authenticating users.

Safely execute custom applications through key and certificate management, security automation, and cloud mobility.
"When we have the right partners, we can help our customers overcome their challenges. ...which is why we are working with AWS and Futurex. They help us provide the innovative, scalable, reliable, and compliant solutions our customers are seeking day after day."
- Thiago Lopes, Information Security Manager
Pismo


Futurex provides HSMs and key management servers that handle encryption, bring-your-own-key (BYOK). Futurex helps enterprise organizations deploy a modern cloud data security environment that complies with the latest standards and regulations.

